Mr_abdi@live.com
hi
http://technet.microsoft.com/en-us/library/cc995114.aspx
Configuring a PPTP Site to Site VPN with TMG 2010
If you have branch offices, you need VPN. Without VPN it will be hard to do file sharing, policies and other stuff. If TMG 2010 is your way to go for this, then read on. TMG 2010 supports multiple protocols for VPN like, IPsec,
L2TP over IPSEC and PPTP. The last one is the simplest type of VPN you can create with TMG, and this is what Im going to show you in this guide. Ill take care of the other two in some future articles. Im going to put my configuration in the table bellow
so you can create an image of whats going on.
|
Site A (Main office) |
Site B (Branch office) |
TMG name: TMG-Site1
Public IP: 208.67.110.10
Internal IP: 192.168.100.254/24 |
TMG name: TMG-Site2
Public IP: 208.67.110.11
Internal IP: 192.168.50.254/24 |
Client Site1
IP: 192.168.100.10/24
Gateway: 192.168.100.254 |
Client Site2
IP: 192.168.50.10/24
Gateway: 192.168.50.254/24 |
To start we need to make sure we have connection between our TMG 2010 servers; do a PING and see if it responds.


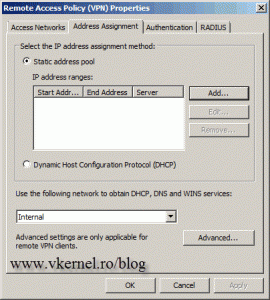
Now open the TMG console from the main office and go to Remote Access Policy (VPN). Here we have a couple of things to set up; first click the Configure Address Assignment Method link
so we can set up how TMG will assign IP addresses to VPN clients.

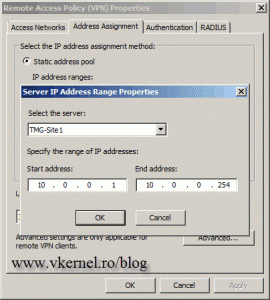
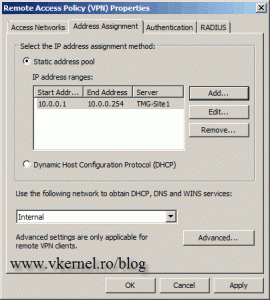
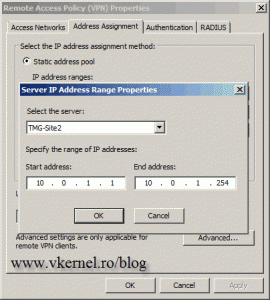
We can choose to use a DHCP server, or a static IP address pool. Right now I dont have a DHCP server for this network, so Im going to choose the static IP address assignment. Click the Add button, select
the server from the drop-down-box, then type the IP address range you want to assign to VPN clients. Click OK when youre done, thenOK again to close the Remote Access Policy (VPN) Properties window.
Back on the TMG console click the Enable VPN Client Access link. If you dont do it, the other TMG server (branch office) will not be able to connect. Click the Apply button
to save the changes to the configuration store.

Now go to the Remote Sites tab and click the Create VPN Site-to-Site Connection link.

Give the connection a distinctive name and click Next.

Choose Point-to-Point Tunneling Protocol (PPTP) and continue the wizard.

After clicking Next, a pop-up opens telling us that a user account must be present on the system with dial-in permissions and that it needs to have the same name as the site we are creating now.

Click OK on the message and open Server Manager. Go to the Local Users and Groups section, right-click Usersand choose New
User.
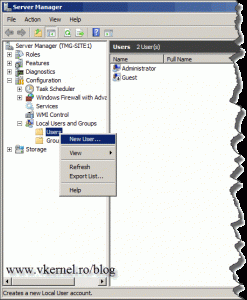
The name of the user must match the name of the site, Site1-to-Site2 in this case. Provide a strong password and check the User cannot change password and Password
never expires boxes then click the Create button.

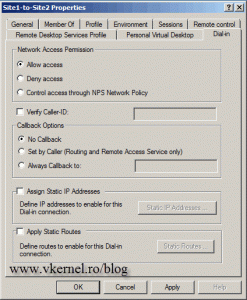
Open the account properties, go to the Dial-in tab and select the Allow Access radio button under Network Access Permission section.
Back on the Create Site-to-Site Connection Wizard, type the FQDN or the IP address of the remote site.

This is a bit misleading, but here we must provide an account name and credentials that exists on the remote site so the connection can be established. Since the TMG server is not part of any domain I will leave the Domain box
empty. The account does not exist right now on the other TMG server, but we need to create it. Because I dont want to have multiples accounts created on a server for one VPN connection Im going to call this account Site2-to-Site1; this will
be the VPN connection name that we are going to create on the branch TMG, later on. You will see when we start configuring the Site2 TMG.

Log in to the branch office TMG server, open Server Manager and create the user account.

Click the Add Range button and type the IP address range of the remote site. If you have multiple IP ranges you need to type them all.


If you are using NLB for the remote site type the IP address of the load balancer, if not clear the box and continue the wizard.

The VPN connection requires a network rule, and here the rule can be created automatically for us. Just click Next to continue.

A Network Access Rule also needs to be created between the site-to-site VPN and the internal network. Most of the times you will allow only the minimum required traffic, but for this example I will allow
all the traffic.

Click Finish to create the site-to-site VPN connection. If a message pops-up that the Routing and Remote Accessservice needs to be restarted, just click OK to
continue; but be careful because if you have users connected trough VPN they will be disconnected once the RRAS service restarts.

Dont forget to hit the Apply button so changes can be saved in the TMG configuration store.

The main office TMG is configured. Its time to go and take care of the branch office server. Everything weve done till now needs to be done again with some small name and IP changes. Open the Site 2 TMG console and set the address
IP assignment first, then enable the VPN client access. The IP address assignment needs to be on a different subnet. When youre done click the Apply button to save the changes.
Give the VPN connection a name; Im going to call this Site2-to-Site1.

At the Remote Site Gateway page, type the public IP address or FQDN of the TGM from the main office.

This is where it gets tricky again. Ive explain it above so Im not going to review it. The account name (Site1-to-Site2) already exist on the main office because we created it during the VPN connection wizard.

After youre done with the wizard, apply the changes to the configuration store then wait a couple of minutes until the connections initialize. Only then the site-to-site VPN connection will work. If you dont want to wait you can
force them by opening the Routing and Remote Access console > Network Interfaces, right-click the VNP interface and choose Connect.

Its time to test and see if is really working. From the main office client ping the client from the branch office, and vice versa.


Create a share on one of the clients and access the share from the other side. That should work to, if not it means you did not allow access trough access rules, or the firewall on the client is blocking the traffic.

































