Hi Machi12,
Welcome to the EMET Support forum.
When you mention that you could never open EMET_Conf, could you be more specific? Also, what version of Windows are you using?
EMET_Conf is a command line utility and usually does not open any window. It sometimes will display a command line window if EMET Notifier has been disabled/removed from Windows start-up and you open the GUI of EMET. The EMET_Conf window then re-configures EMET to start EMET Notifier once again at Windows start-up.
In the following thread, I provide examples of using EMET_Conf to protect Windows Media Player with all mitigations and with SEHOP and Mandatory ASLR disabled. Have you had any success in using EMET_Conf in this manner?
http://social.technet.microsoft.com/Forums/en-US/emet/thread/d319ca4a-51df-4ed2-9204-856dbf15a07e
The purpose of EMET Notifer included with EMET 3.5 Tech Preview was to write EMET related events to Windows Event log and to display a pop-up notification in the lower right corner of your screen if an exploit was blocked or a program was incompatible with the specific mitigations applied to it. If everything is working as intended i.e. no application compatibility issues and no exploits are detected, EMET Notifier will not display a notification pop-up. EMETs event logging is discussed in more detail in the following thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/05f9a3eb-6f47-446c-96e1-1db231fef13b
I realize that this thread is for EMET 4.0 Beta event logging but there are a lot of similarities.
My suggestion would be to verify that you can see EMET events in the Windows Event Log, if so, EMET Notifier is working correctly.
One reason why there may be no EMET events in the Windows Event log would be the following:
The reporting functionality of EMET Notifier can be disabled as follows:
Open Regedit
Navigate to the following key:
HKLM\SOFTWARE\Microsoft\EMET
Create a new DWORD value called NotifierLogLevel and set it to 0
This is mentioned on Page 28 (Section 5: Advanced Options) of the EMET 3.5 Tech Preview Users Guide (a PDF file located in the folder where you chose to install EMET into).
To re-enable EMET Reporting, you can simply delete this DWORD value and restart your PC.
You do not have to use EMET_Conf to properly configure EMET to protect the applications you use the most, its functionality is primarily aimed towards deploying EMET on many computers and setting it to protect a pre-defined list of applications using a script similar to what is mentioned in the following thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/d6a8a945-ea55-4970-8b83-f31f4225085b
You can tell if EMET is protecting a program by opening the EMET GUI and looking for a green tick mark for that programs process. This is briefly mentioned in the following thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/56d4edf8-f250-4aea-9c93-72a25d5bfd0e
Using Sysinternals Process Explorer is also an option as mentioned in another thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/88135f86-6414-4a10-a458-848d463bc608
You are correct about the system wide SEHOP mitigation that you disabled, it can sometimes result in application compatibility issues. Setting it to Application Opt-In means disabled unless the application specifically wishes to use it (resulting in better compatibility with applications).
A list of the vast majority of known compatibility issues with EMET are listed in the following thread (apologies if you have already referred to this):
http://social.technet.microsoft.com/Forums/en-US/emet/thread/1e70c72b-67b2-43c4-bd36-a0edd1857875
For your information, the final version of EMET 4.0 is scheduled for release on the 14th of May 2013 (if all goes according to plan) as mentioned in the following blog post:
http://blogs.technet.com/b/srd/archive/2013/04/18/introducing-emet-v4-beta.aspx
UPDATE 9th May 2013: According to the following blog post, the final version of EMET 4.0 has been delayed by 2 weeks and is now scheduled for release on the 28th of May 2013:
http://blogs.technet.com/b/srd/archive/2013/05/08/emet-4-0-s-certificate-trust-feature.aspx
I hope the above information is of assistance to you. If you require any further assistance or advice, please let us know. Thank you.
Hi JamesC . I followed your suggestion and reset IE using MS Fix it tool . Now I can reply as I intended to do a couple of days ago . I guess my security settings were set way too high . It seems one has to strike a balance between security and usability no matter what you do on the internet . I have run into this many times before ( not just with IE but many other types of software as well ) . This is probably what allows viruses to proliferate much more readily . I will have to go back into my IE settings later when I have more time and see exactly which setting(s) were causing the javascript void error . I thank you for so kindly solving this problem for me . Below is my reply to your reply to my original post which thankfully I am now able to post . Thank you . Machi
Hi . Thanks for your reply . I am running Windows 7 X64 Home Premium . I looked at emet logging in Event Viewer . The only things it logs are when I change the emet settings for any process or if emet stops . It never shows if an application has conflicts with emet and as I mentioned earler emet notifier never has popped up a warning of any kind even when a program crashes . I am unsure if I should add the entry to the registry as you suggest . I am hesitant tampering with registry settings as I have no real experience with that .
You ask what happens when I try to open emet conf . A command prompt window briefly opens and disappears instantly . I have never been able to use the command line because of this . However I followed a couple of the links you kindly provided and was able to use the command prompt as admin to enter emet commands . I really thank you for this as I have been trying to figure this out for some time . I only wish I could get emt notifier working . The following are the only entries in the registry pertaining to emet :
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EMET\emet_gui.exe NAME : C:\Program Files (x86)\EMET\EMET_GUI.exe TYPE : REG_SZ
DATA : {bb0dddbf-e4f8-4764-ae59-c7ae9e46bfa8}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EMET\emet_notifier.exe NAME : C:\Program Files (x86)\EMET\EMET_notifier.exe TYPE: REG_SZ DATA : {9b315a25-9543-4e36-a783-5edc02ba1283}
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EMET\emet_conf.exe NAME : C:\Program Files (x86)\EMET\EMET_Conf.exe TYPE : REG_SZ DATA : {273e6351-2cc4-413e-8a7e-c91aad5535b4}
Thanks again . I really appreciate it . Machi
Hi Machi12,
Thanks for your update.
From what I can tell, your EMET event logging seems to working correctly. I also never receive notifications from EMET Notifier since it has not encountered an attempt to exploit any of my applications and only rarely conflicted with any of my applications.
Below I provide screenshots of my EMET Event log. You can see information messages from EMET whenever the PC is restarted or turned on each day:


Direct Links to Images:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/EMET_Event_Log1.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/EMET_Event_Log2.png
The warning message is about a change that I made to the configuration of an application, namely Skype by enabling the EAF mitigation. At the time I was trying to cause EMET Notifier to create a notification but Skype worked even with the known problematic EAF mitigation that is mentioned at the beginning of the Application Compatibility thread. Skype has continued to work correctly. My Skype version is 6.3.0.105. I dont recommend others try this setting, but it seems to work fine for me.
Warning messages are created in the log anytime the EMET settings of an application change or a program is removed from the list of protected applications, here is another example:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/EMET_Event_Log3.png
This was created when I uninstalled Logitech SetPoint from my PC and so no longer needed EMET to protect it.
When you first add an application to the EMET list of protected applications, an information message is created. Here is an example showing me adding one of several files after updating my Python installation from 2.7.3 to 2.7.4:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/EMET_Event_Log4.png
Finally, here is an old error message about Dropbox not being compatible with the EAF mitigation of EMET 3.0:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/EMET_Dropbox.png
Please note that EMET Notifier will not always show a notification in the lower right corner of your screen when it conflicts with a program. On these occasions Windows will simply display an error message that a program was closed unexpectedly (and lists the name (and filename) of that program). This usually happens after installing a new program and adding it to the list of applications for EMET to protect. If that program is not compatible with a mitigation of EMET, you will need to change the EMET settings for that program until it works correctly.
Dont be concerned with the change to the registry that I mentioned above. Such a change is not standard practice and would only be necessary if you wanted to stop EMET from creating events in the Windows Event log. I mentioned it simply as a potential cause of why EMET may not be creating entries in the event log.
For your reference, please find below a screenshot my EMET 3.0 settings from the following location in the registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EMET

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/EMET_3_Reg_Settings.png
Please note that list of keys (that look like folders) on the left side of this screenshot (below the EMET key) are actually the names of program files (executables) that are protected by EMET. I have a very large number of non-standard files protected by EMET. So you can ignore this list shown in the screenshot.
The registry entries that you copied into your above post seem to show that you have added the components of EMET to be protected by EMET namely, emet_gui.exe, emet_notifier.exe and emet_conf.exe
You dont need to add these files since they are compiled according to the Microsoft SDL and already incorporate mitigations such DEP, ASLR and /GS (among others)
As for EMET_Conf you will only need to use this if you wish to use scripts e.g. VB or batch scripts to add the names of files that you wish to protect with EMET. This can just as easily be done from the EMET GUI. The scripts are usually used in a corporate environment where an IT administrator wishes to deploy a standard list of programs for EMET to protect to hundreds or thousands of computers at a time.
EMET _Conf is also used for protecting applications whose location on your computer may vary from time to time using wildcards e.g. the Folding@Home client from Stanford University places executable files in various locations while processing research work. I added the names of these files using a batch script containing the following commands:
EMET_Conf.exe --set "*\FahCore_15.exe" EMET_Conf.exe --set "*\FahCore_a3.exe" EMET_Conf.exe --set "*\FahCore_a4.exe"
This saves me from having to change the list of protected files as the locations of these files can change over time. The filenames are always are the same, only their location varies. Since the above commands only use the filenames (which dont change) EMET will always protect these files no matter where they are located.
For your information, the use of wildcards is discussed on the following pages of the EMET 3.0 Users Guide. This is a PDF file located in your EMET installation folder, which by default is one of the following paths:
32 bit Windows: C:\Programs Files\EMET 64 bit Windows: C:\Programs Files (x86)\EMET
Page 15: Section 2.1: Protection Profiles
Page 18 - 19 : Section 2.3 : EMET Command Line Tool
Another example of using wildcards is provided in the following blog post (see section Recommended applications to add):
http://www.rationallyparanoid.com/articles/microsoft-emet-3.html
e.g.
EMET_conf.exe --set "*\firefox.exe"
Not everyone is going to have a use for this functionality of EMET, its use is optional.
As I mentioned above, EMET 4.0 is due for release in 2 weeks time. I have been using the EMET 4.0 Beta version on some test PCs but the remainder of my PCs still use EMET 3.0. I will upgrade them once the final version of EMET 4.0 is available.
UPDATE 9th May 2013: According to the following blog post, the final version of EMET 4.0 has been delayed by 2 weeks and is now scheduled for release on the 28th of May 2013:
http://blogs.technet.com/b/srd/archive/2013/05/08/emet-4-0-s-certificate-trust-feature.aspx
Apologies for my very long post above but I wished to answer all of your questions. If you need any further assistance, please let us know.
Thank you.
Hi Machi12,
Youre right. EMET is very effective at stopping malware exploits as well as zero day exploits that may be discovered and exploited in the future.
The effectiveness of EMET (backed up with some statistics) is discussed in the following thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/4589a620-f93c-4c11-b9fe-54d15feff331
As for the new mitigations that are available with EMET 3.5 Tech Preview. The reason for them not being enabled by default or "out of the box" was they were experimental defenses against ROP (Return Oriented Programming) attacks. Thus this makes 3.5 work the same as version 3.0 unless you change the settings.
EMET 4.0 Beta has refined these new mitigations and in general they offer better compatibility and performance than the same mitigations of EMET 3.5 Tech Preview. EMET 4.0 Beta also includes newer mitigations that 3.5 Tech Preview did not. As I mentioned full details on whats new in version 4.0 are available in the blog post about EMET 4.0 Beta that I linked in my first post in this thread. In 2 weeks time, the final version should be available.
EDIT: For your information, the use of wildcards is discussed on the following pages of the EMET 3.5 Tech Preview Users Guide. This is a PDF file located in your EMET installation folder, which since you are using 64 bit Windows will be:
64 bit Windows: C:\Programs Files (x86)\EMET
These page numbers are slightly different to that of the EMET 3.0 User Guide (mentioned above).
Page 15 - 16: Section 2.1: Protection Profiles
Page 19 - 20 : Section 2.3 : EMET Command Line Tool
Feel free to experiment with the newer ROP mitigations and/or trying out EMET v4.0. If you have any questions or issues, please create a new thread (question) on this forum and we will be happy to assist you.
Thank you again for marking my post above as an answer. Its very much appreciated :)
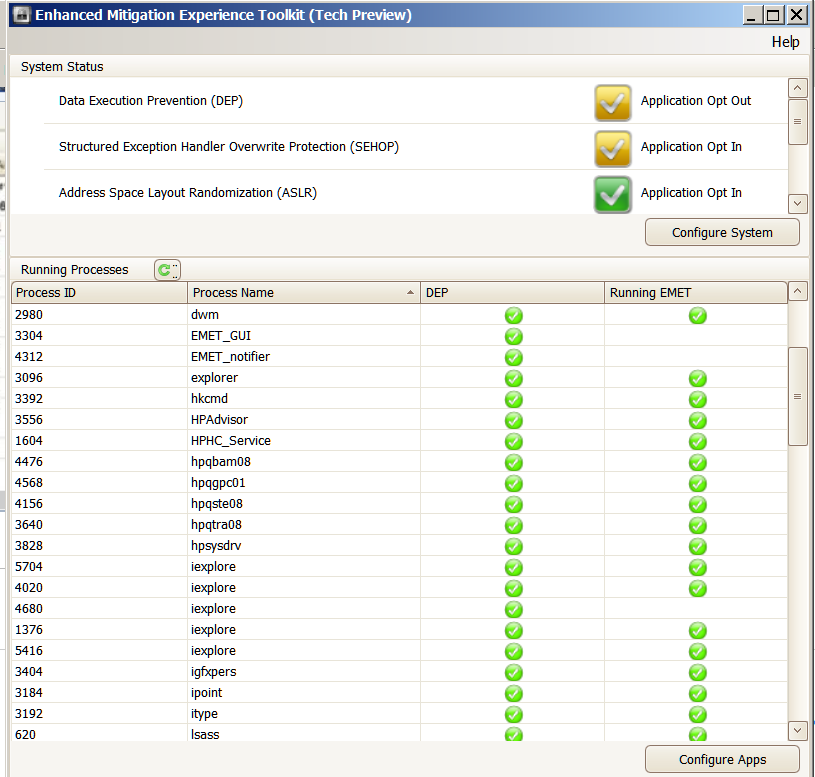
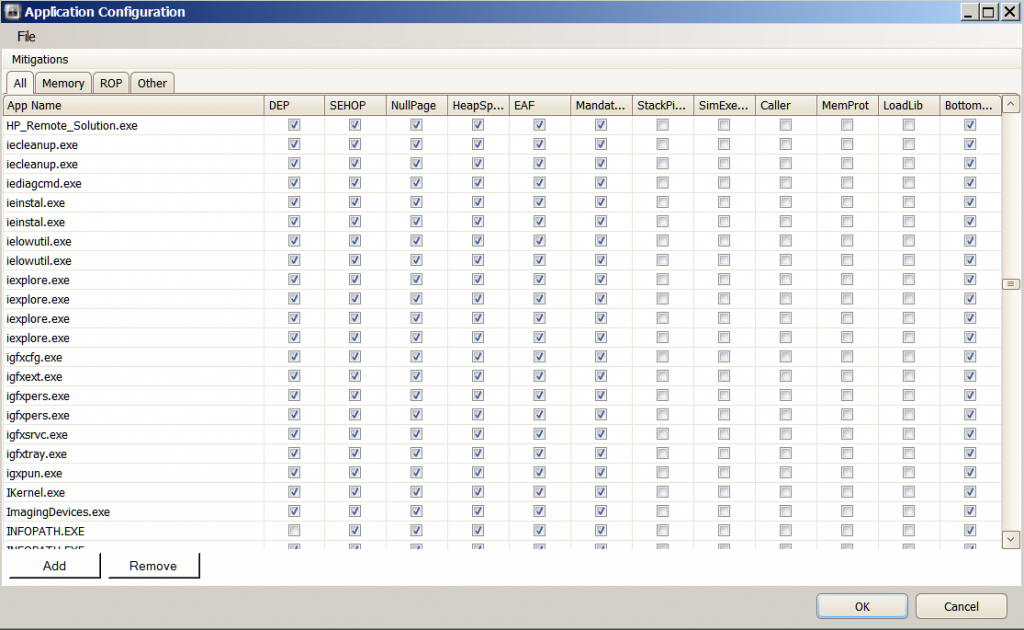
Hi JamesC . Here are my screenshots of EMET . As you can see one instance of IE is shown as not protected by EMET . The Application Configuration shows IE as being configured . These screenshots were taken at the time of my original post . Currently this problem has not reoccurred . I didn't change any of the settings so I have no idea why it has not happened again . One problem I have currently noticed is that when I enter EMET_Conf --list in the command prompt it does not display all the application mitigation settings that I have configured EMET for . It only shows ( listed alphabetically ) the applications from U to Z . It does not show the applications from A to U . The Application Configuration in the EMET GUI shows all the applications from A to Z . Again I have no idea what this means ? Thanks again for all your help . Machi
Hi Machi12,
My apologies for not replying to you sooner. My availability/time has been limited lately and my responses are delayed due to this.
You are correct, I can see the instance of IE not being protected by EMET in your screenshot, I am unsure why.
One strange observation that I note from your screenshot of the Configure Apps window is that you have 4 instances of iexplore.exe. Even on a 64 bit PC, only 2 instances are required, if you configure iexplore.exe to be protected using the Add button of the Configure Apps window. Only 1 instance is needed if you use the following command:
EMET_Conf.exe --set *\iexplore.exe
If for any reason you encounter an instance of IE (iexplore.exe) not being protected by EMET, I would suggest using the above EMET_Conf command.
I describe this in more detail in my post dated May 2nd in your other thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/20893f6a-d239-4872-810a-6de9e297016e
As for the issue with EMET_Conf.exe --list, this is expected behavior. Using this command on my PC (which has over 300 programs opted into EMET) results in only in the letters from T to Z being shown:


Direct Links to Images:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/CMD_3.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/CMD_4.png
I have taken some screenshots that show some of the items in that list.
This is expected behavior since by default the Command Prompt window has a text buffer size of 200 (50 x 4 (Buffer Size x Number of Buffers)). When this limit is reached, the command prompt window simply starts from the beginning and overwrites the buffers contents with any remaining text that it needs to display.
I assume this translates to 200 lines of text. I also assume that each entry in the list of EMET protected apps is 2 lines long when displayed in the command prompt window.
Counting the number of entries from an exported XML config file from my EMET installation, from the beginning screenshot showing TrueCrypt.exe to the end final screenshot showing zip.exe was exactly 99 programs in length.
You can increase the size of the buffer as follows:
Open a command prompt using the steps mentioned in the following thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/d319ca4a-51df-4ed2-9204-856dbf15a07e
Click in the upper left corner of window (where the black icon is located) and from the menu that appears choose Properties:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/CMD_1.png
In the Options tab, in the Command History section, use the arrows to increase one or both of the options for Buffer Size and/or Number of Buffers and click OK when you have completed this:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/CMD_2.png
Further information on these settings is provided in the following links:
You can direct the output of the command prompt window to a text file in a location of your choice as follows. This file will contain the entire command prompt output. The following command will list all of the applications protected by EMET and will place it in a file on your Desktop. You can also place the file in another location of your choice e.g. your Documents folder:
C:\Program Files (x86)\EMET>EMET_Conf.exe --list > "%userprofile%\desktop\emet_list.txt" C:\Program Files (x86)\EMET>EMET_Conf.exe --list > "%userprofile%\documents\emet_list.txt" C:\Program Files (x86)\EMET>EMET_Conf.exe --list > C:\emet_list.txt
Here is a screenshot of a file that I created using the first command (above):

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/EMET_List_File.png
Please note that since the command prompt is running under the Administrator account, the file will be placed on that accounts Desktop (which may not be the same account you are logged into the time). For this reason I have chosen to show a third command that will place the file in location that you can access using any account (note that this file will be placed on the root of your C Drive).
As I mentioned you can change the location to any folder that you choose and call the file any name that you choose.
For your information, using the EMET_Conf.exe --list command will result in the same list of protected applications that you see in the Application Configuration (Configure Apps) window) that you provided a screenshot of in your previous post.
I find an easier method of backing up/documenting this list of protected applications is to use the Export command and create an XML file that contains this list in textual form:
From within the Application Configuration (Configure Apps) window, click the File menu in the upper left corner and choose Export and place the XML file with a name of your choice in a folder/location of your choice:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/EMET_Export.png
As I mentioned in the following thread, EMET 4.0 Beta has moved this option to a different location:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/acd338d2-c06c-42f7-97a6-b8ee422f7dde
One final observation is that you have added Windows Explorer (explorer.exe) to the list of applications protected by EMET. I have seen 2 examples of other EMET users encountering issues with this configuration and it is an application that I do not protect with EMET for this reason:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/1e70c72b-67b2-43c4-bd36-a0edd1857875
http://social.technet.microsoft.com/Forums/en-US/emet/thread/86cb7c58-b1ac-4ae8-b9b9-688f729eef23/
For the first link above, please see the posts dated, the 1st of February 2013 by Lucas Z. _ and myself. However, please feel free to leave EMET protecting explorer.exe if you find it works well for you.
I hope the above information is of assistance to you and answers your questions. If you have any further questions, please let us know. Thank you.
Hi everyone,
I wanted to provide some clarification on why I have chosen to protect such a large number of programs using EMET on my personal system. I mentioned in my previous post above that there are over 300 individual executables protected by EMET on my PC. Please allow me to explain why I have chosen to protect this extremely large number of executable files:
My suggestion of using EMET for as many applications as possible is due to the advice on pages 16 and 40 of the PDF linked to below i.e. that attackers focus will now switch to less hardened applications and applications that load at predictable locations in memory.
Matt Miller (Microsoft) Exploit Mitigations of Windows 8:
http://media.blackhat.com/bh-us-12/Briefings/M_Miller/BH_US_12_Miller_Exploit_Mitigation_Slides.pdf
My thanks to Chris Covington for originally linking to the ISC blog post containing a link to this PDF.
In addition, many 3rd party applications that we use every day do not implement some or any security mitigations and it is for this reason as well as the predictions in the above PDF that I feel we need to harden as many applications using EMET as possible. The techniques used by recent zero day flaws e.g. in January and May this year that rely on DLLs being loaded at predictable locations is also an indicator that these mitigations are becoming increasingly important.
The fact that many 3rd party applications do not use even basic mitigations such DEP should in the future become less of an issue since for example as mentioned in a Microsoft whitepaper, Visual Studio 2010 (I would assume the 2012 version has similar defaults) adds common security mitigations to applications built with it by default unless the application developer explicitly turns them off, see the table on Page 19 of the following whitepaper:
http://www.microsoft.com/en-us/download/details.aspx?id=26788
Its disappointing to see that many applications still do not take advantage of these mitigations as mentioned in a quite recent security news article:
However it is not all bad news, for example the open source VLC Media Player has supported DEP and ASLR for a number of years:
http://unhandledexpression.com/2010/07/02/current-state-of-security-in-vlc-on-windows/
Other applications such as Apple QuickTime, Apple iTunes, Foxit Reader, Adobe Reader, Google Chrome and Mozilla Firefox and other popular applications do include permanent DEP and ASLR which is very encouraging to see.
In my opinion, every 3rd party application should at least implement permanent DEP and ASLR (which should also include ASLR support for each DLL that this application uses). If an application supports more mitigations than this, that is good news. I do not expect every 3rd party program to implement the large quantity of mitigations that EMET 3.0 or EMET 4.0 include.
While I absolutely do not expect the vast majority of EMET users to take such a strict approach to how many applications they protect with EMET since it can be time consuming and you are very likely to encounter compatibility issues. Everyone should find the settings that work the best for them.
To reach this number of (executable) .exe files protected by EMET, I would simply add all .exe files from the program folders of any 3rd party application that I used. Gradually (after testing if each application still worked as expected) I added more applications until no 3rd party running process on my system was not protected by EMET. I was surprised how easy this was and how few compatibility issues I encountered.
Apologies for writing such a long explanation (and for going off-topic) but I hope it serves to demonstrate why I have taken this approach.
Thank you.
Hi JamesC . Thanks for clearing up my confusion as regards to EMET_Conf --list . I had looked at the properties and saw the buffer size and number of buffers options . However I did not want to change anything as I was unsure . Thank
you for also showing me how to direct the output of the command prompt window to a text file . What does the " discard old duplicates " option do and what is the difference between " quick edit mode " and " insert mode "
?
I read the thread on explorer.exe that you directed me to . I mentioned in my very first post above that some programs ( including explorer exe. ) were freezing ( not responding ) frequently . I eliminated the vast majority of these
freezes by changing SEHOP ( System ) to Application Opt In from Application Opt Out . I didn't change anything else . I left all Application Configurations exactly as they were . My question is will this leave my system more vulnerable and
to what extent ? Does this mean that the applications which were crashing for which SEHOP is enabled are now opting out of SEHOP protection ?
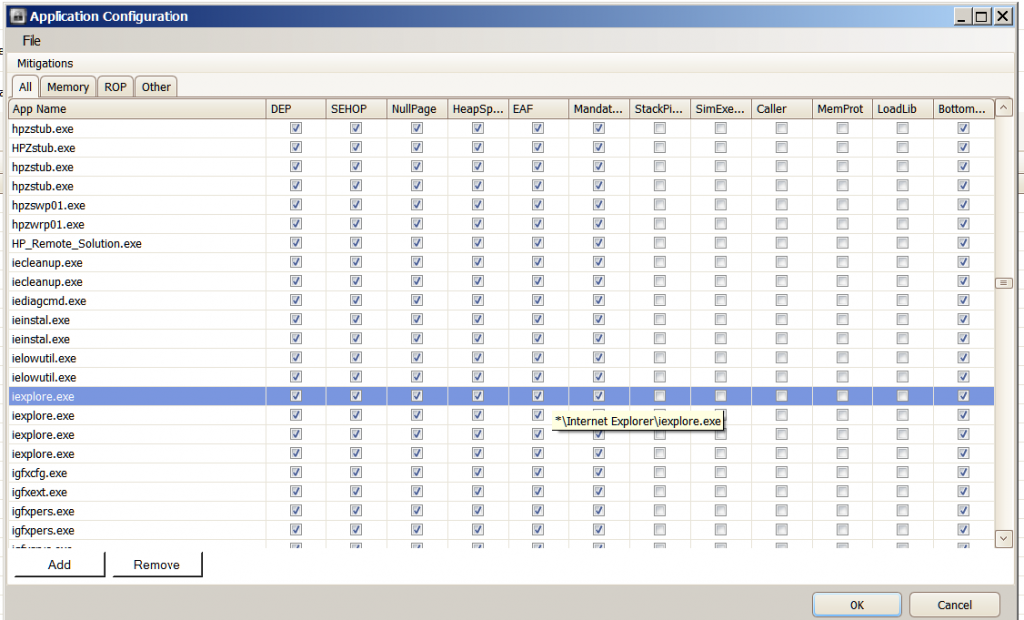
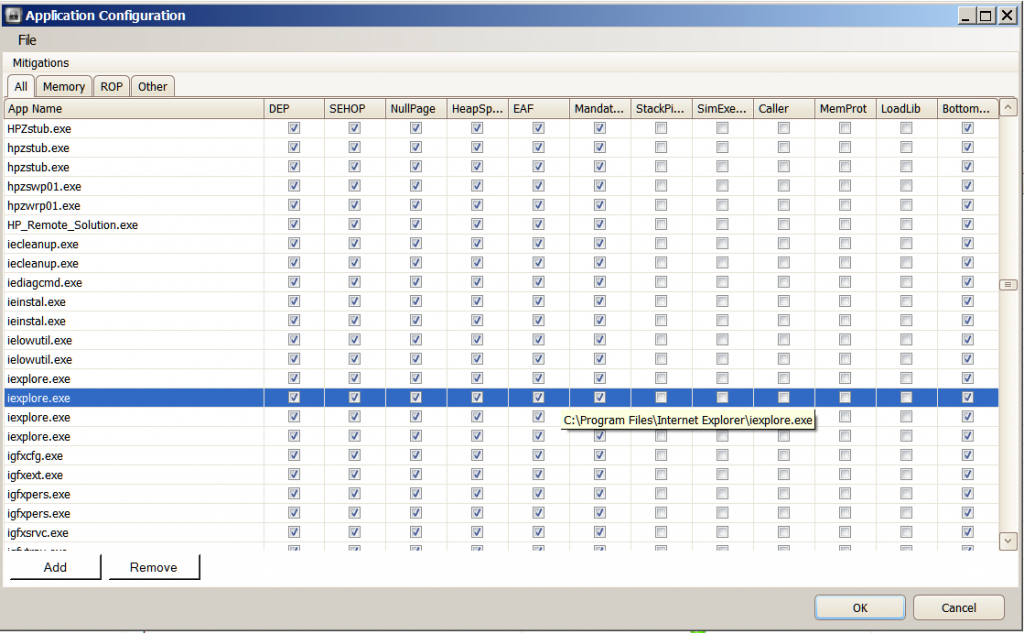
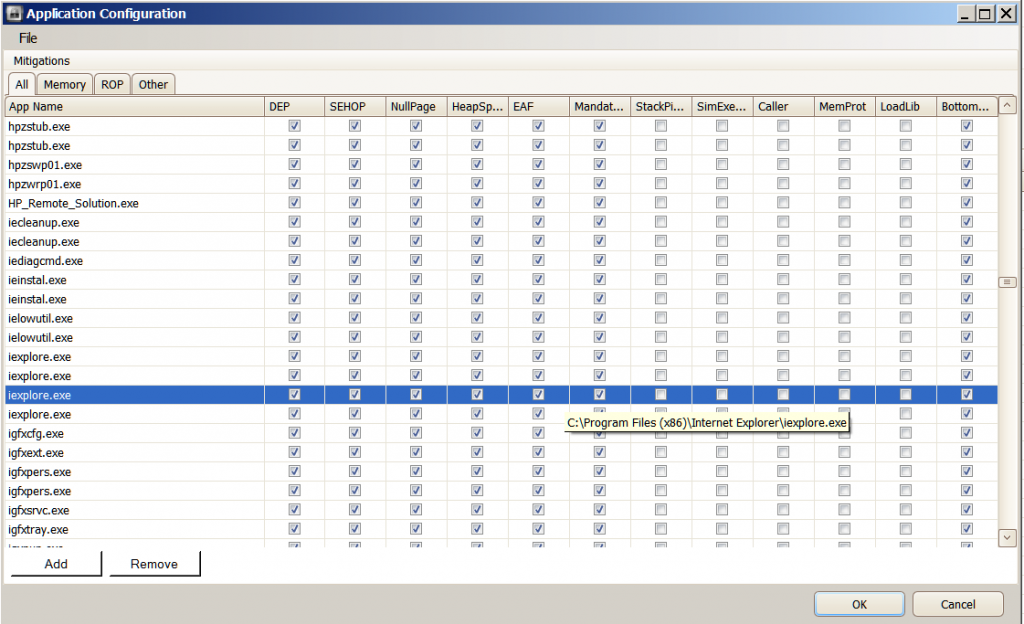
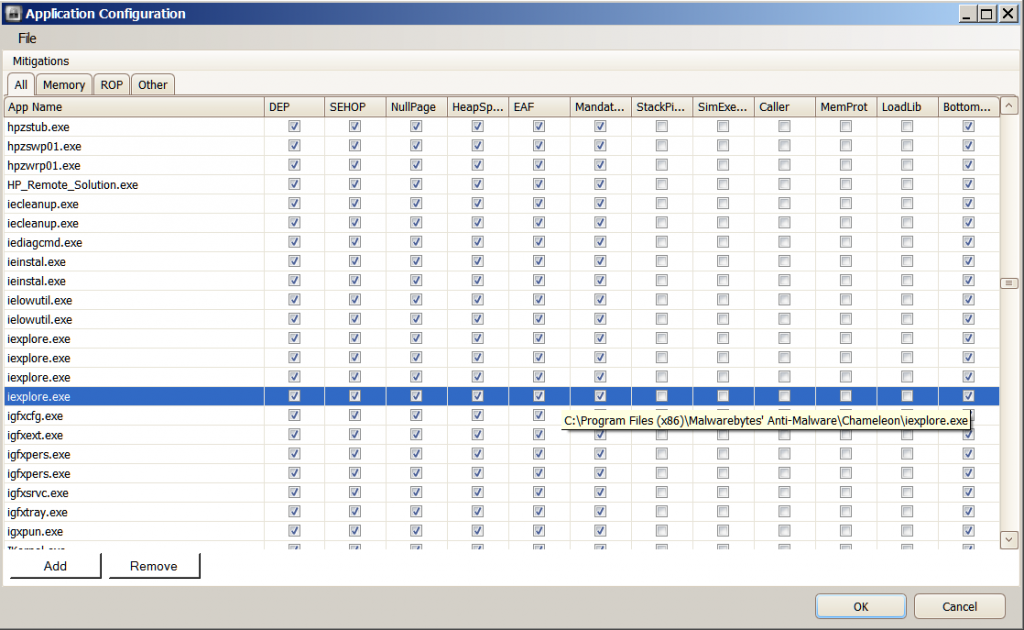
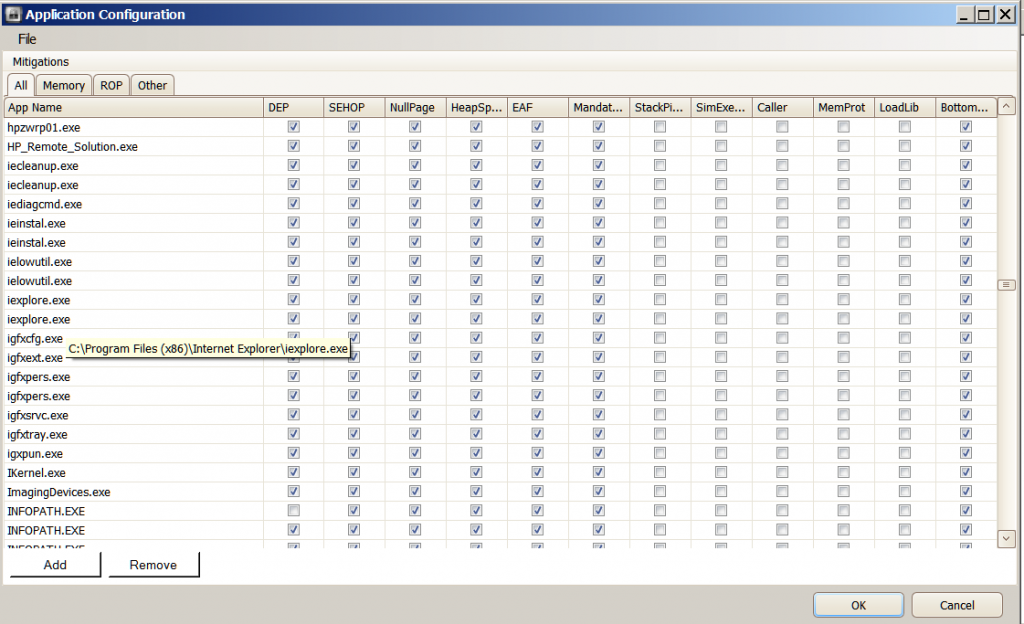
The problem of IE showing an instance of not being protected by EMET has reoccured . I am including screenshots below . I have shown four screenshots of the Application Configuration window because it was the only way I could think of at the time to show exactly what the path is to each IE process being protected . As you can see the path *\ Internet Explorer\iexplore.exe is one of the paths . You had suggested using the command prompt to include this path . Is it necessary to do that since it is already shown in the Application Configuration ? This was not added by me using the command prompt but was included in the preconfigured Deployment//Protection Profiles/Internet Explorer XML and was added when still using EMET 3.0 . The vast majority of the other Configurations were done by me using the " ADD " feature when I was using EMET 3.0 . Since changing to EMET 3.5 I haven't added any more . I always open IE ( X64 ) In-Private from the taskabar . Then I either open other instances of IE by clicking on links from within webpages , by opening pages from my favorites bar or by typing directly into the address bar . I exclusively use IE X64 and In-Private browsing .
You mention that you have over 300 individual executables protected by EMET. When I was still using EMET 3.0 I had added a huge number of executables to EMET protection . I haven't counted them exactly but it is several times the number you mention . These are still being protected by EMET 3.5 . I am wondering if this is overkill on my part ? In addition should I disable all protection for explorer.exe except for DEP, ASLR and /GS (Guard Stack) v2 which you mention in your thread that you directed me to ? /GS (Guard Stack) v2 I am not familiar with . I assume explorer.exe is automatically configured with this enabled and it is not part of the EMET configurations ? Thanks again for all your help . Machi
To be more correct I should have said " Does this mean that the applications which were crashing for which SEHOP is enabled are now not opting into SEHOP protection ? " instead of " Does this mean that the applications which were crashing for which SEHOP is enabled are now opting out of SEHOP protection ? "
Hi Machi12,
Thanks for your update.
In relation to your questions about the configurations options related to the Command Prompt, here is some information that you may find useful:
Discard old duplicates:
In the Command Prompt, you can use the Up and Down arrows of your keyboard to scroll through a list of recently used commands and the Discard Old Duplicates checkbox will delete duplicated commands from the list.
Source: http://samanathon.com/customize-the-command-prompt/
Quick Edit Mode:
Explained in the following post:
http://tweaks.com/windows/36732/command-prompt-quick-edit-mode/
Insert Mode:
This setting (which is on by default) allows you to insert text at the cursor position. Clearing the Insert Mode check box setting will allow you to overstrike characters instead.
Source: http://technet.microsoft.com/en-us/magazine/ff758104.aspx
My thanks to the authors of these articles for this useful information.
-------------------------------------
You are correct about the SEHOP system wide setting, it can introduce compatibility issues. I have this setting enabled but have needed to turn it off when installing some programs, the installers simply wont start unless I do.
Turning off this setting would reduce your systems protection but since you have EMET enabled for the vast majority of your programs, they are benefitting from per process SEHOP protection of EMET. Thus your overall protection is not reduced.
If any program is not compatible with the SEHOP protection of EMET, disabling it is the right thing to do since you are using that program for a task that you wish to complete. If leaving this setting enabled makes the program crash every time the program is useless. You will still have the remaining 6 mitigations of EMET 3.0 and also the remaining 5 mitigations of EMET 3.5 Tech Preview protecting that program(which is formidable protection). When EMET 4.0 is available you will have the new Deep Hooks, Banned Functions and Anti Detours mitigations protecting it too. So I would not describe such a program as then being vulnerable.
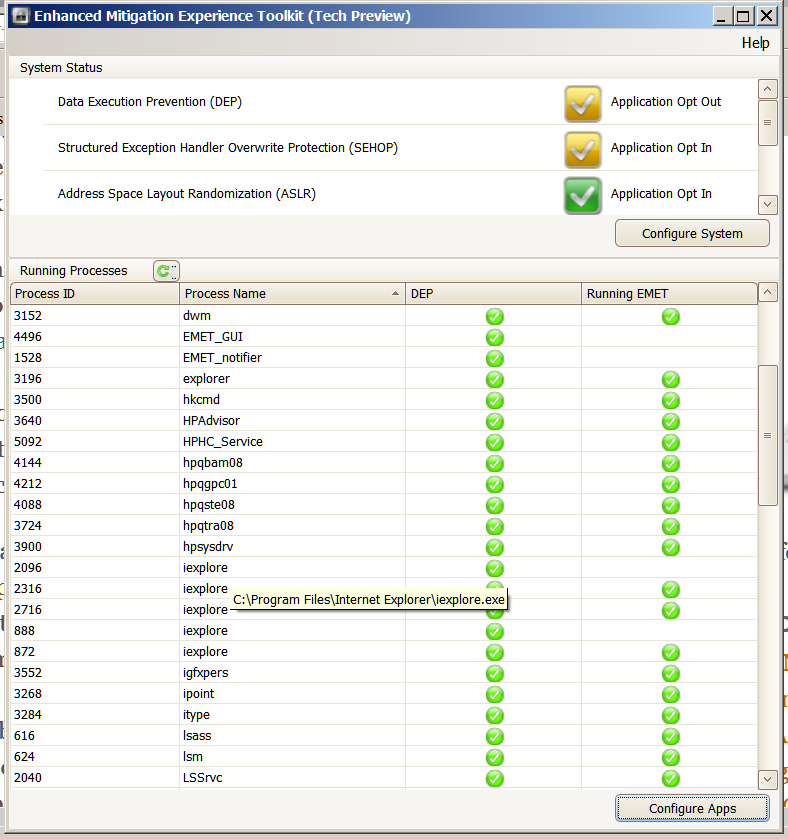
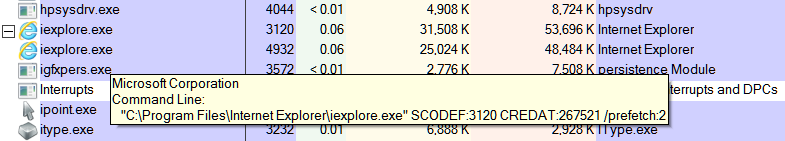
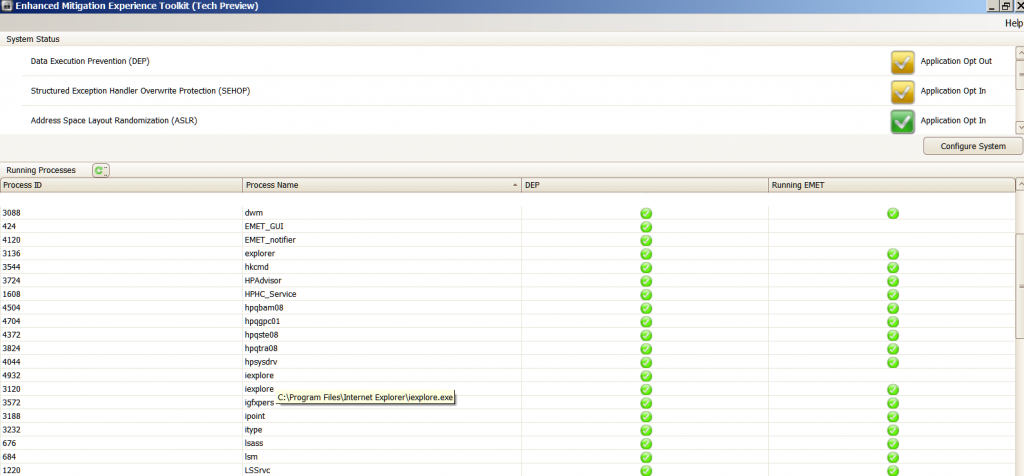
In an effort to narrow down what is causing that single instance of IE to not use EMET; if it happens again, could you provide a screenshot of your EMET status screen that also shows what path this instance is located within? The path will appear when you hover your mouse over the word iexplore. The following screenshot demonstrates what I am referring to:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_Path_EMET_35_HL.png
If possible, could you then match the Process ID of this instance (shown on the left of the above EMET status screen) and highlight this instance within Sysinternals Process Explorer and also show its path by hovering your mouse over it. The Process ID 3620 appears in both screenshots:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_Path_ProcessExp_HL.png
Process Explorer is a separate program that you need to download. The good thing is that you don't install it, you simply extract it (i.e. unzip/decompress) to any location of your choice and double click procexp.exe to run it.
Thanks for your screenshots; the first 3 show a slight overlap in how EMET is applying protection to iexplore.exe. I might suggest removing that overlap in the future. The paths shown in the screenshots are correct, so should not be causing an issue.
I am anticipating that one or both of the above tests will show us why EMET is not protecting that instance of IE. If neither shows anything wrong, I would wait until EMET 4.0 is available and then test again if this still occurs. If it does, you can submit a bug report describing the issue and reference this forum thread for the screenshots it contains. The email address to send this report to is mentioned in the final paragraph of the following blog post:
http://blogs.technet.com/b/srd/archive/2013/04/18/introducing-emet-v4-beta.aspx
In addition, how you launch and use IE 64 bit seems fine and should not be causing this issue.
As for the number of programs/executables being protected by EMET. I am in the minority when I say no number is overkill. I protect any 3rd party program that I use as well as any frequently running program on my PC. In addition to the reasons that I gave above, reading the following blog post reinforced even further to me, that this is a good idea (although not all programs mentioned are the latest versions):
http://0xdabbad00.com/2012/12/05/finding-slop-common-windows-apps-still-without-dep-and-aslr/
My response to your question would be that however many programs/executables that you wish to protect is up to you. If you can manage that number and are not experiencing any issues with those programs, then I do not see a problem. You did mention freezes at the beginning of your previous post, if you would like advice on how to resolve these freezes for any affected programs, I would be happy to assist you.
With regards to explorer.exe, if EMET is not causing any issues with it you can leave EMET protecting it. The reason that I mentioned it in my previous post was to point out that while EMET can protect explorer.exe without issues, it is not always that simple. It is one of the top most likely programs to experience compatibility issues with EMET.
To clarify, explorer.exe is part of Windows and has been created according to the Microsoft SDL process which means that it includes DEP, ASLR and /GS protection (among other protections) by default (without any interaction from EMET) which you correctly pointed out above. /GS is built into it and cannot be turned off.
I hope the above explanations answer your questions. If I can provide any further assistance, please let me know. Thank you.
-------------------------------------
If you are interested, I have provided some references that describe what /GS (Guard Stack) cookie protection is below:
Matt Miller (Microsoft) Exploit Mitigations of Windows 8:
http://media.blackhat.com/bh-us-12/Briefings/M_Miller/BH_US_12_Miller_Exploit_Mitigation_Slides.pdf
Pages 5, 11, 12, 35 mention /GS.
http://blogs.technet.com/b/srd/archive/2009/03/20/enhanced-gs-in-visual-studio-2010.aspx
http://blogs.msdn.com/b/sdl/archive/2011/12/02/security.aspx
Analysis of /GS protections in Windows Vista:
http://www.symantec.com/avcenter/reference/GS_Protections_in_Vista.pdf
This PDF was part of a series of whitepapers that I read many years ago about the new defences introduced with Windows Vista:
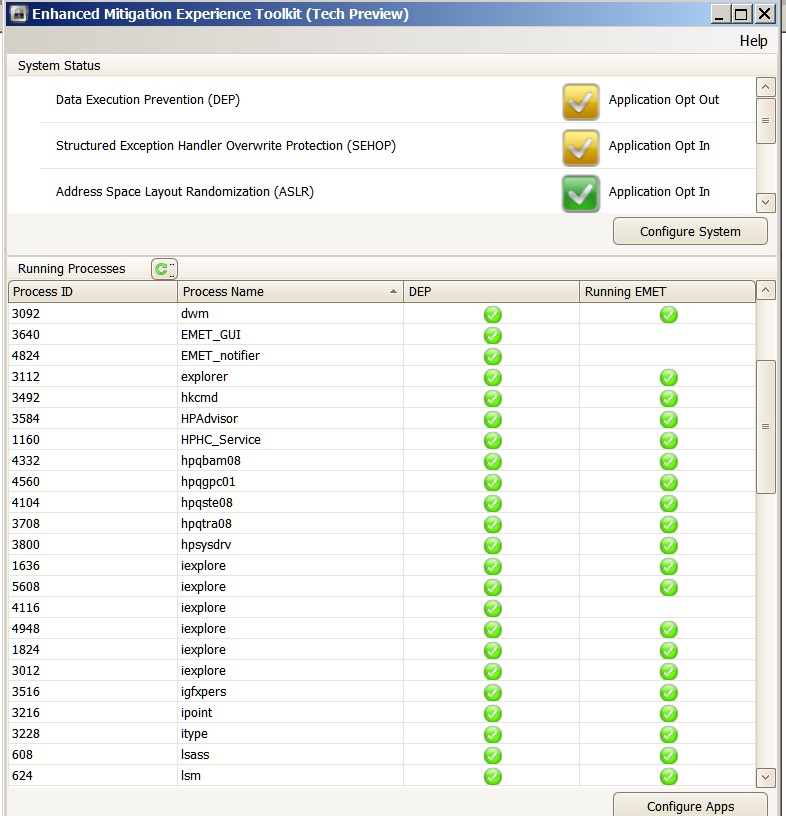
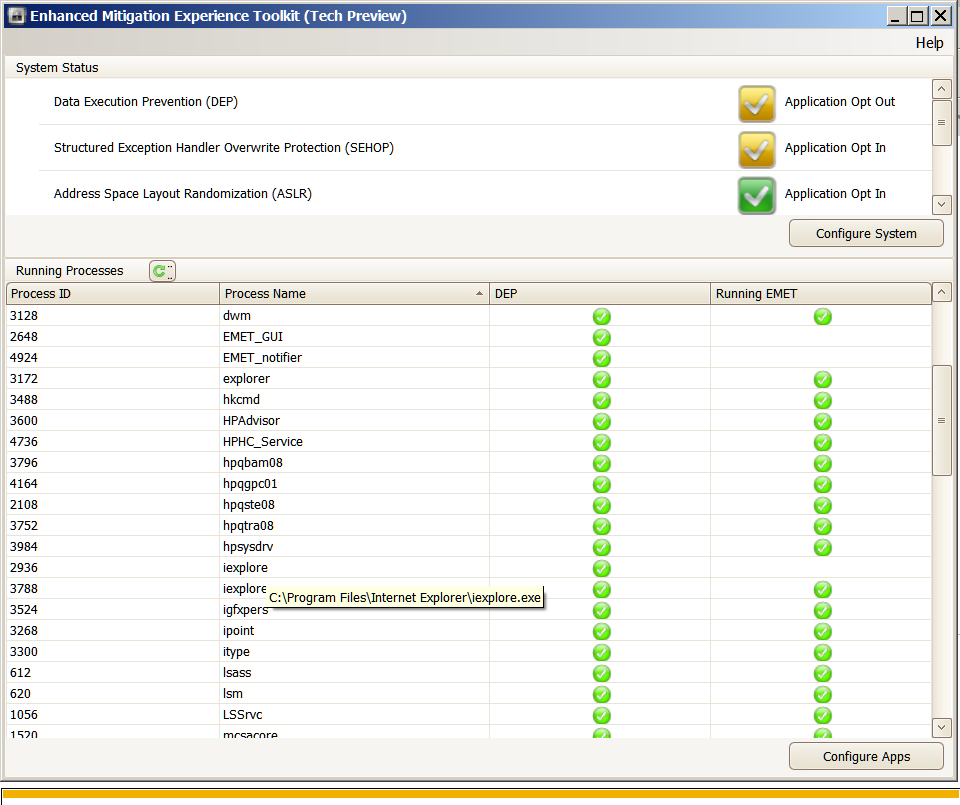
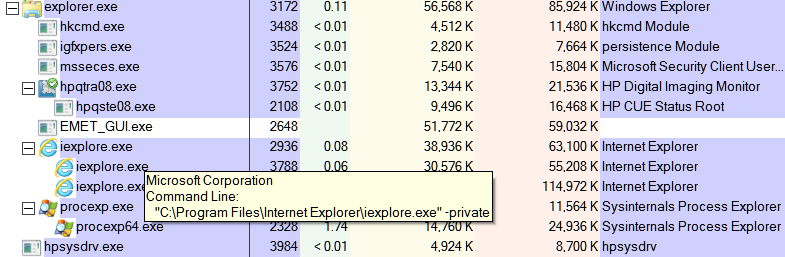
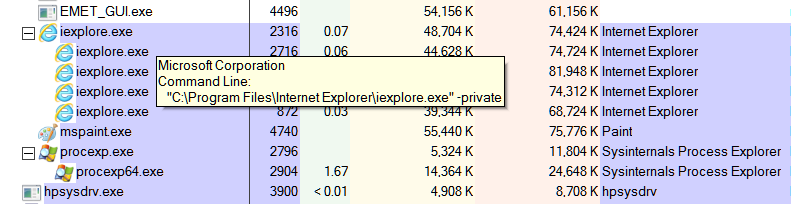
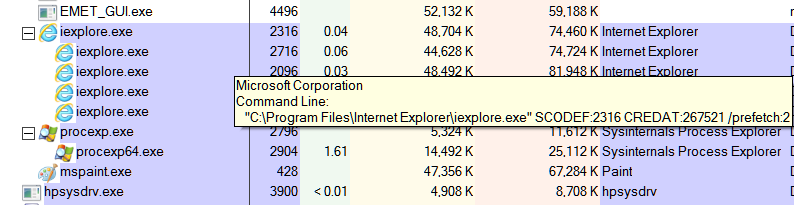
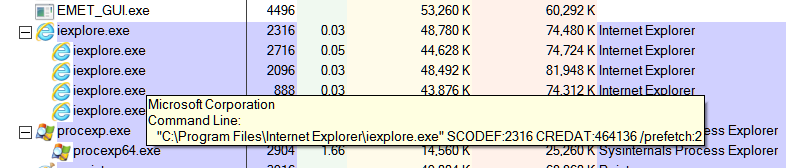
Hi James C . Here are the screenshots . I only had one instance of IE (10 ) X64 open at the time of the EMET screenshot . I have included a screenshot of this page . The EMET screenshot shows two instances of IE : Process ID
2936 ( not protected by EMET ) and Process ID 3788 ( protected by EMET ) . I had already opened another instance of IE ( clicking the EMET Forum link pinned to my Favorites bar ) before I ran Process Explorer ( which you recommended in your reply ) .
Thus the third instance of IE( 2928 ) showing in the Pricess Explorer screenshot which does not show in the EMET screenshot . I hope these screenshots help narrow down what is happening here .
I would also like to thank you for answering my other questions about the command prompt , changing SEHOP to opt-in from opt-out and also the numerous references you provided . Machi
Hi Machi,
Thanks for the extra screenshots. I was hoping that they would show something out of place but the information they contain shows no reason why 1 instance of Internet Explorer is not being protected by EMET.
From the previous set of screenshots that you provided, there were 4 entries for iexplore.exe within EMETs configured applications window (although I am aware that one of them belonged to Malwarebytes Anti-Malware Chameleon, a tool that I have used before).
What I am going to suggest may sound like back-tracking/repeating myself (apologies if it does) but I feel we need to match the settings that you are using with settings that I am using which are working as intended. This may not achieve anything but it will at the very least serve to narrow down what is causing this issue.
Could I ask you to remove the following 2 entries for iexplore.exe from the screenshots that you provided?


Just to reassure you, I obtained the links to your images using the IE Developer Tools toolbar (accessible by pressing F12 and choosing Images->Show image paths). Eric Lawrences Fiddler tool could have shown this information too. These links are available since they need to be loaded by IE when it displays this thread.
When these changes have been carried out, your EMET configured applications window should look similar to the following:


Direct Links to Images:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_EMET_35_1.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_EMET_35_2.png
As you can see using these settings, I cannot reproduce/replicate the behavior that your EMET installation is showing:


Direct Links to Images:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_InPrivate_EMET_35_HL.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_InPrivate_ProcessExp_HL.png
You and I are using the same version of Windows 7 64 bit SP1, the same version of IE 10 and the same version of EMET (3.5 Tech Preview) with the same mitigation settings (i.e. all 5x ROP mitigations disabled for IE).
My only remaining suggestion if the above steps fail is remove all entries for iexplore.exe and replace them with one entry created using the command prompt:
Follow the instructions to open a command prompt window as mentioned in the following thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/d319ca4a-51df-4ed2-9204-856dbf15a07e
The final command you will enter using the command prompt will be (ignore the command for Windows Media Player in that thread but do include the set of double quotes ""):
EMET_Conf.exe --set "*\iexplore.exe"
This one command will have the same effect of using the original 4 entries that you currently have i.e. it will Internet Explorer and protect the Malwarebytes Chameleon tool since it shares its name with Internet Explorer.
I have needed to use the command prompt approach when adding some applications to EMET since adding them using the GUI and the Add button results in EMET not protecting the application even after restarting that application (this is very rare). I have found this behavior corrects itself after several reboots but using the command prompt to protect that application usually fixes it right away (I am unsure why).
If EMET is still experiencing this issue when you are now only using the 2 entries or just 1 entry for iexplore.exe I would suggest waiting until EMET 4.0 is available (currently scheduled for the 28th of May, if all goes according to plan). You can then check if it still shows this issue. If it does, (as mentioned in my previous post above) you can then submit a bug report for it.
If the email address for feedback regarding EMET 4.0 changes from its current address for EMET 4.0 Beta, I will update this thread showing where to obtain the new address.
While I may have exhausted all of my suggestions to resolve this issue, I will continue to provide assistance to you in whatever means that I can to see that this issue is resolved for you. As always, if I can assist with any further questions, please let me know.
Thank you.
Hi Machi,
A short update, I noticed that your system wide security settings were different to mine.
DEP Set to: Application Opt Out
SEHOP: Set to Application Opt In
I changed them to match yours and then rebooted. Unfortunately I still cannot replicate the issue with IE that you are experiencing:


Direct Links to Images:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_InPrivate_EMET_35_SWSettings_HL.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_InPrivate_ProcessExp_SWSettings_HL.png
Thank you.
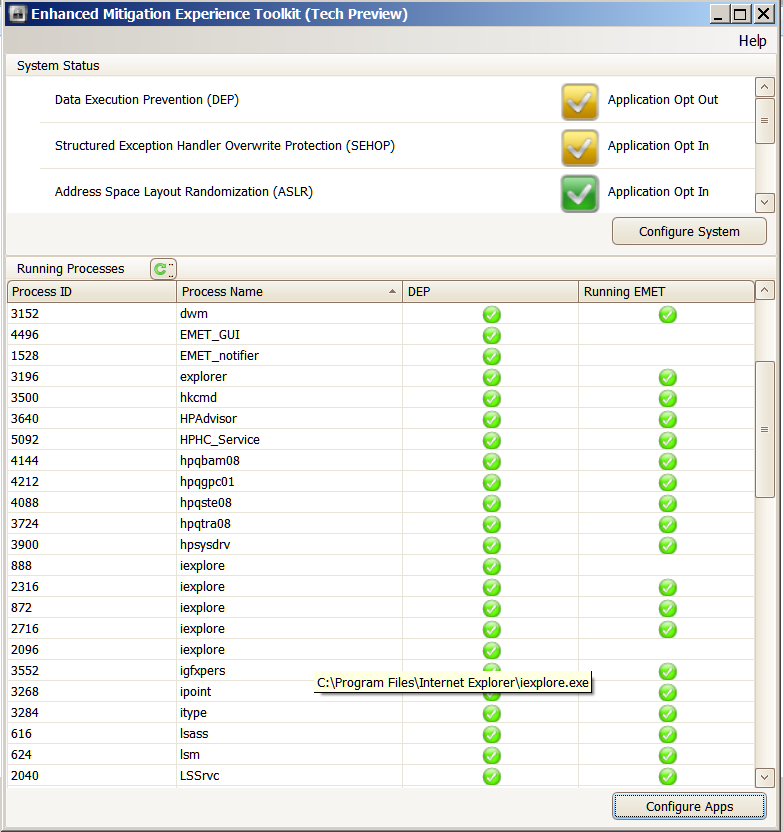
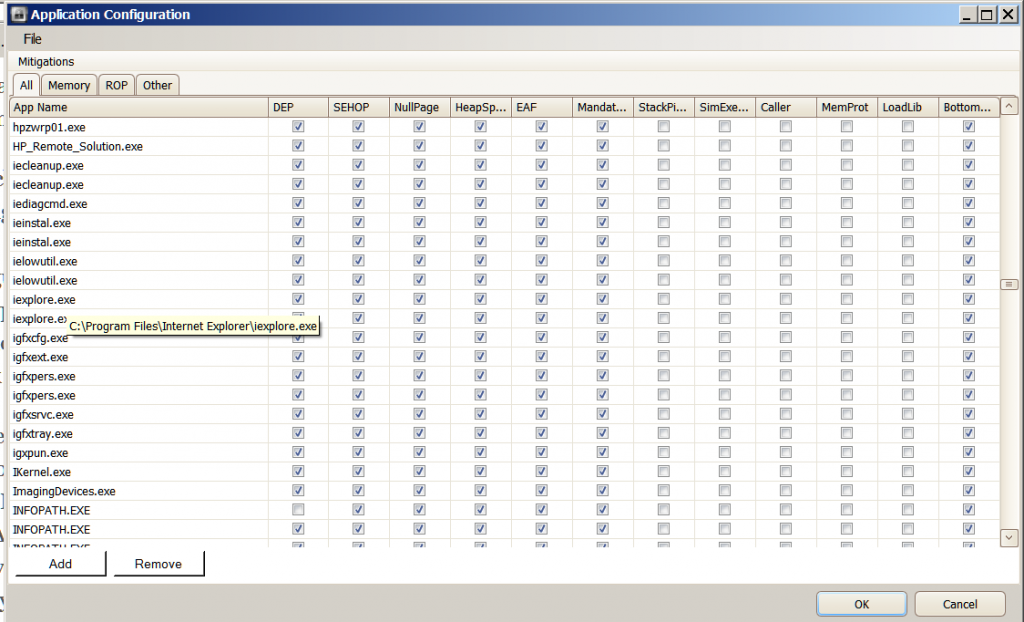
Hi JamesC . The problem has occurred again with the new settings . This time two instances of IE are showing as not protected by EMET . I have provided screenshots . Perhaps they will show what is happening this time . Let me know if you need any more info . Machi
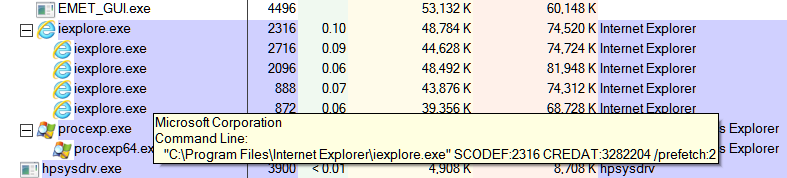
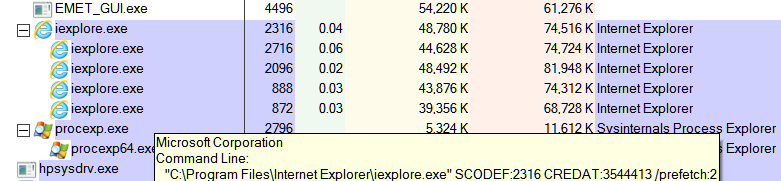
Hi Machi,
Thank you for your additional screenshots and for taking the time to provide them in this thread. Unfortunately, all of the information that they show is normal and does not provide any insight into what could be causing this. This is proving to be a difficult to diagnose/troubleshoot issue.
Thanks for following my advice on reducing the number of entries for iexplore.exe in the Configure Apps window to just 2. This has ruled out that the other entries were causing this issue.
My apologies but I dont have any other suggestions to troubleshoot or resolve this.
You mentioned that you would try my suggestion of using the Command Prompt to add iexplore.exe to the list of Configured Apps, did this step resolve this issue? (I have provided a copy of this suggestion at the end of this post for your convenience).
If the issue is still present, I would like to request that you try the final version of EMET 4.0 when it becomes available on the 28th of May (which should resolve this issue). I hope that waiting on this release does not cause you any inconvenience.
If EMET 4.0 (final) still shows this behavior a bug report can then be submitted. Alternatively if you wish to try EMET 4.0 Beta and it still shows this behavior, a bug report can then be submitted right away.
Thank you.
-----------------------------------------------
Suggestion from my previous post:
Remove all entries for iexplore.exe and replace them with 1 entry created using the command prompt:
Follow the instructions to open a command prompt window as mentioned in the following thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/d319ca4a-51df-4ed2-9204-856dbf15a07e
The final command you will enter using the command prompt will be (ignore the command for Windows Media Player in that thread but do include the set of double quotes ""):
EMET_Conf.exe --set "*\iexplore.exe"
This one command will have the same effect of using the original 4 entries that you currently have i.e. it will Internet Explorer and protect the Malwarebytes Chameleon tool since it shares its name with Internet Explorer.
-----------------------------------------------
Hi Machi,
I wanted to provide some further information that may be of assistance when you choose to upgrade to EMET 4.0:
I am unsure if upgrading from 3.5 Tech Preview to EMET 4.0 will be a supported upgrade path. This info should be provided when EMET 4.0 is released.
If it is not a supported upgrade path, following these steps should enable a smooth upgrade (I have used these to upgrade from 3.5 Tech Preview to 4.0 Beta without any issues):
Uninstall your current version of EMET via the Windows Control Panel
Manually delete the following registry keys:
HKEY_LOCAL_MACHINE\Software\Microsoft\EMET HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\EMET
Please note that the second key listed above may/may not be present. If the second key is not present, simply proceed to the next step. If it is present, delete it as mentioned below.
I realize that you are using Windows 7, but I have provided steps for each version of Windows should other forum members wish to make use of them.
Removing keys from the registry can be performed using Regedit which can be opened as follows:
-----------------------------------------------
Windows XP:
Open Windows Regedit as follows:
Press the Start button in the lower left corner of the screen. Click Run.
Type regedit (without the quotes) into the white line of the Run box that appears. Click OK.

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/WinXP_Regedit1.png
-----------------------------------------------
For Windows Vista or Windows 7:
Press the Start button in the lower left corner of the screen. Type regedit (without the quotes) into the white search box just above the Start button.

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Windows7_Regedit1.png
A blue cube icon with the title regedit will appear near the top of the Start menu, right click this icon and choose Run As Administrator. Click OK or Continue if prompted by Windows User Account Control (UAC) to open Regedit.
-----------------------------------------------
For Windows 8:
Press the Windows Key (between the Ctrl and Alt keys in the lower left corner of your keyboard), to display the Start screen.
Type the word regedit (without the quotes) you should see an icon for Regedit (a blue cube) appear on the left side of your screen:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Win8_Regedit1.png
Right click this icon and choose the Run As Administrator (that appears at the bottom of the screen).

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Win8_Regedit2_HL.png
Click OK or Continue if prompted by Windows User Account Control (UAC) to open Regedit.
-----------------------------------------------
For All Versions of Windows:
1.Once Regedit is open, navigate to the above registry key locations (keys are represented as folders). From the screenshot below you can see I have navigated to the following key:
HKEY_LOCAL_MACHINE\Software\Microsoft\EMET

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Win8_Regedit3.png
2. Right click the key you wish to delete and choose Delete. Answer Yes to the following question:

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Win8_Regedit4.png
Are you sure you want to permanently delete this key and all of its subkeys?

Direct Link to Image:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Win8_Regedit5.png
3. Repeat steps 1 and 2 (if necessary) for the remaining registry key.
4. Begin the installation of EMET 4.0 by double clicking the EMET Setup.msi file that you have downloaded and follow the instructions to complete the installation.
-----------------------------------------------
Please note: while the screenshots that I have provided above (in the For All Versions of Windows section) were created using Windows 8,any other version of Windows should look very similar to these.
I hope this helps. Thank you.
Hi Machi,
Apologies for not replying sooner.
I will let you know how this works out.
Yes, please do.
I am very interested in this since it is an unusual issue especially since the screenshots you have kindly provided do not directly point to the cause i.e. the EMET settings are normal and the information from Process Explorer was also perfectly normal.
Thanks for your understanding and continued efforts.
------------------
EDIT: 23rd May 2013: I located the following EMET Support thread that also mentions a similar issue with EMET 3.0 not protecting Internet Explorer. Unfortunately the issue in that thread was never resolved:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/a80ae20a-83fd-46a8-a21e-b4de67448cc4
Hi JamesC . I only had one instance of IE 10 X64 open ( In-Private ) when I took the screenshots . As you can see from Configure Apps I had IE protected by EMET by using the command prompt . Superficially Process Explorer doesn't seem to show anything amiss . I looked at the Properties for that instance of IE and it showed EMET64.dll ( Path : C:\Windows\AppPatch\AppPatch64\EMET64.dll ) as present . I am not all that familiar with using Process Explorer so I am not sure what else I should look for to see if anything is amiss . Perhaps you could let me know . Thanks again . Machi
I just noticed your edit mentioning the other EMET thread . I will have a look at it . Thanks . Machi
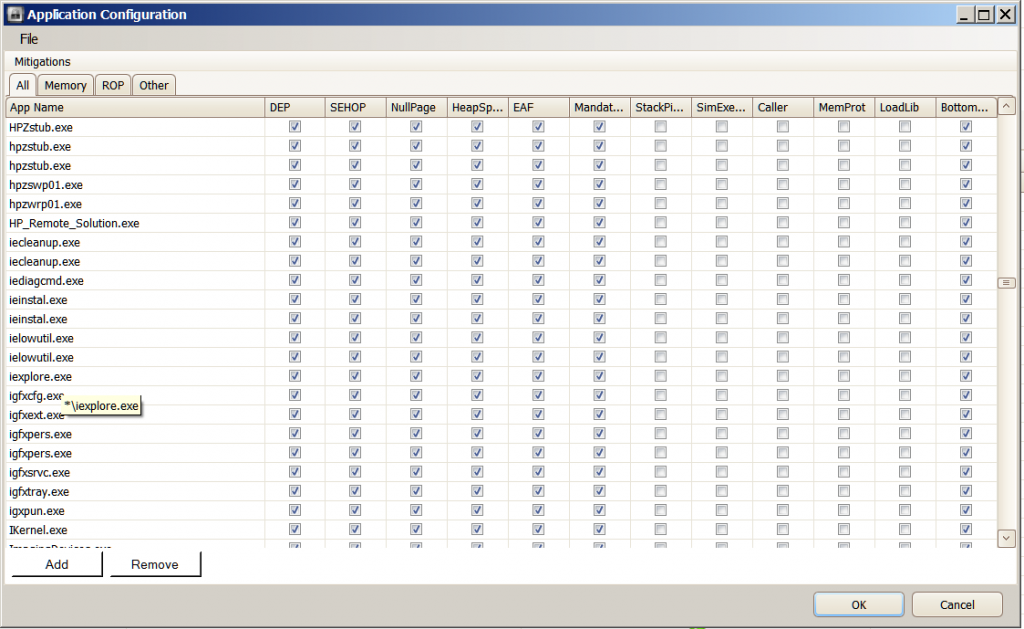
Hi Machi,
If you are seeing EMET64.dll present within iexplore.exe with the same process ID as the instance of Internet Explorer that EMET is showing as not protected (from your screenshots this is 4932) then this is good news.
From what you have mentioned, you are correct in that once EMET64.dll is present, nothing is amiss. As long as the EMET64.dll is present, you are protected.
From what I can tell, if EMET is showing that iexplore.exe is not protected but Process Explorer shows EMET64.dll is present. Thus EMET is simply not displaying the correct information.
For your information, EMET64.dll should be present within every instance of iexplore.exe as shown by the screenshots below:



Direct Links to Images:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_EMET_35_ProcessIDs_HL.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_EMET64_1_HL.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/IE10_EMET64_2_HL.png
As you can see, the process IDs are 3408 and 4084 and Process Explorer shows EMET64.dll is loaded within each process.
If you are seeing the same result within Process Explorer, you are protected.
I hope this explanation helps. If I can provide any further clarification or assistance please let me know. Thank you.
Hi Machi,
The fact that EMET64.dll is present in each instance of iexplore.exe is really good news. You are correct, since EMET does not show it is protecting every instance of iexplore.exe that is a bug.
It will be interesting to determine if EMET 4.0 shows this bug, if it does you can report it.
You are also correct about EMET Notifier, what you describe is indeed its purpose. From my experience I can confirm what you mention. Not all conflicts with EMET are displayed by EMET Notifier. Sometimes even the Event log will not show the error (when viewing EMET related events). I found this to be the case on my Windows Vista 64 bit SP2 PC. Many of the 3rd party programs would crash with EMET enabled but EMET Notifier would not notify. Sometimes the event log would show what happened. The vast majority of the time, I would need to disable the mitigations one by one until the program worked again.
Apologies that I did not clarify this behavior when I previously mentioned this. For my Windows 7 PCs, I have only ever experienced an issue with earlier versions of Dropbox which conflicted with the EAF mitigation of EMET. Recent versions of Dropbox work fine with EAF enabled. At the time, EMET Notifier did not display a pop up in the lower right corner of the screen but the Event log did show the conflict.
If you wish, I can re-enable the mitigations on my Vista PC and test if EMET Notifier and/or the Event Viewer show this behavior. It was last Summer when these conflicts occurred and I am re-calling what happened. At this time that PC still has EMET 3.0 installed. I intend to install EMET 4.0 probably next weekend. In the next 6 to 9 months I will replace this PC with a Windows 8.1 equivalent.
I am not sure about a way to correct the logging/notification behavior of EMET. From what I can tell, not all programs trigger such notifications/events in the log but I could be wrong.
-----------------------------------------------
To anyone else reading this thread:
What is your experience of the success of EMET Notifier? Do you find it notifies you of conflicts that your configured programs have with EMET? Does the Event Viewer show this information? Any comments/additional input would be much appreciated.
-----------------------------------------------
To Machi:
I hope what I have mentioned above is of some assistance to you. I am not entirely satisfied with how EMET notifies the person of conflicts either but I have only encountered conflicts just after installing EMET on a PC and once resolved, that shortcoming is no longer an issue. The variety/number of programs on my PCs tend to stay the same i.e. I am not adding more on a regular basis (although I do keep my existing program up to date).
I would suggest that you provide your suggestions to the Microsoft EMET team by sending an email to the address mentioned at the end of the following blog post:
http://blogs.technet.com/b/srd/archive/2013/04/18/introducing-emet-v4-beta.aspx
I have been testing EMET 4.0 Beta since its release and have not experienced a conflict with any 3rd party program that I use (so far). Thus unfortunately, I cant tell if this notification/logging behavior has improved.
If I can provide any further assistance/clarification, please let me know. Thank you.
Hi Machi,
Last weekend I installed Windows 8 Pro 64 bit on my PC. I used the clean install method and kept none of my applications from my previous Windows 7 Ultimate 64 bit SP1 installation.
I have now been able to reproduce the EMET status error that you have been experiencing with EMET 3.5 Tech Preview. I have found this issue occurs with the final version of EMET 4.0.
Please find below screenshots showing the issue. As you can see, Process Explorer shows the true status of EMETs protection of IE 10. I have also shown the file handles of EMET64.dll to prove that Process Explorer is showing the correct information (file handles need to be allocated and de-allocated correctly or data loss and/or instability will occur and are thus less likely to have been written incorrectly.)






Direct Links to Images:
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Microsoft_EMET_40_IE10_Status_Error_HL.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Microsoft_EMET_40_IE10_Status_Error2.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Microsoft_EMET_40_IE10_Status_Error3.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Microsoft_EMET_40_IE10_Status_Error4.png
http://i742.photobucket.com/albums/xx69/Jimboc/Microsoft/Microsoft_EMET_40_IE10_Status_Error5.png
IE 10 on my system is running with Enhanced Protected Mode enabled and is the desktop version of IE (not the Modern UI version).
My EMET config only has a wildcard version of IE added. I have found this type of EMET config entry less likely to experience an issue.
I am unsure if the above information is of assistance to you, but it shows that this issue is not just isolated to EMET 3.5 Tech Preview.
I dont believe this issue to be serious since EMET is actually protecting IE even if the EMET status panel does not show this. However the EMET status panel is showing misleading data. I have sent a link to this thread to the EMET Feedback email address.
Thank you.


